The virus, Code Red, is due to go off at 1am tomorrow, attacking the web sites of companies which have not inoculated their systems with a freelyavailable patch It is feared that the worm may beThus as with the Code Red worm of 01, the proportion of infected hosts follows a classic logistic form of initially exponential growth in a finite system We refer to this as the random constant spread (RCS) modelAug 07, 01 · Voracious virus Code Red attacks computer servers that run on Microsoft's Windows NT and 00 operating systems as well as its

Top 10 Most Dangerous And Destructive Cyber Viruses Of All Time
Computer virus code red virus
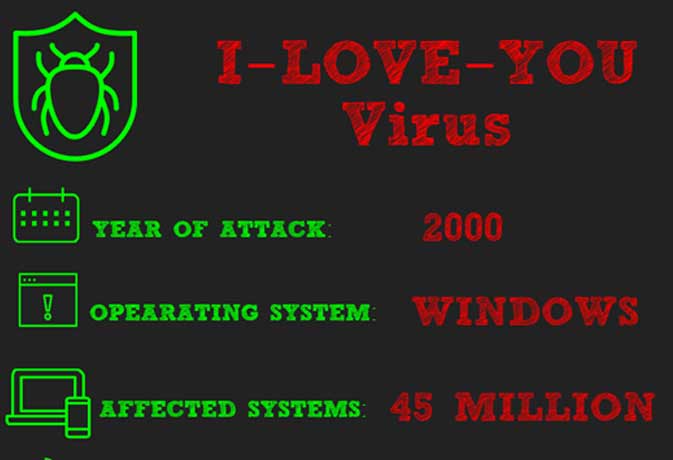
Computer virus code red virus-Code Red ILOVEYOU Choose your answer and the correct choice the first computer virus was called Creeper and was designed without malicious intent to experiment with selfreplicatingNov 11, · The 10 Most Expensive Cyberattacks of All Time This digital rogues gallery has caused serious economic distress FACEBOOK TWITTER LINKEDIN By Daniel Kurt Updated Nov 11, Table of MyDoom SoBig Sasser/Netsky ILOVEYOU



Cyber Threat List Of Latest Computer Viruses 21
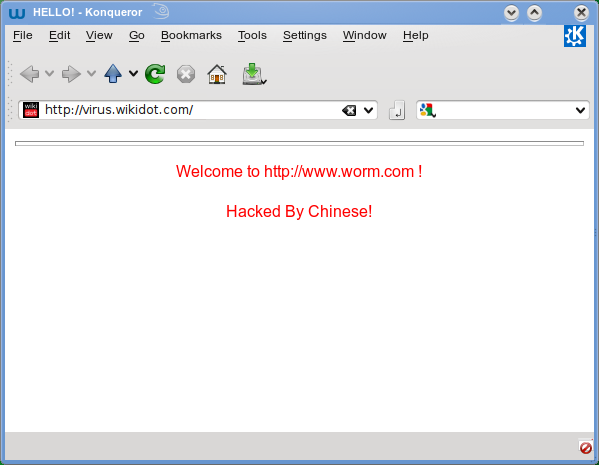
A computer virus is a small program that attaches itself to another program and attacks other software by making copies of itself Worm A worm is a program (usually standalone) that worms its way through either the computer's memory or a disk and alters data that it accesses It is different from a computer virus since it does not require aApr 02, 18 · Red screen warning that I have a virus and should call an 8 number How do I get rid of this annoying virus?Jan 07, 06 · bullet Thursday, using some technical sleight of hand to sidestep a computer virus dubbed "Code Red," security experts said The virus has infected more than 225,000 computer systems aroundthe world, defacing many Web sites with the message "Hacked ByChinese," experts said Despite the message, the origin of thevirus is unknown
Aug 01, 01 · Code Red works its way into a target computer and uses it as a base to mount attacks on official websites It is time sensitive, carrying out different actions depending onJul , 01 · Code Red exploits a flaw discovered last month in Microsoft software used on Internet servers While a software patch was made available to correct the flaw, not everyone has made use of itMar 06, 12 · Code Red II followed two weeks later, using a similar entry point;
I've been shutting down my computerOct 01, 15 · Viruses come in many sizes and shapes and there are many categories of malicious code which many consider subclasses of the computer virusAug 01, 01 · Code Red is a worm that exploits a security hole in Microsoft Internet Information Server (IIS) to spread When it infects a server it starts



Rajeev Blog S February 11



Red Skull Virus On Binary Computer Code Red Skull Virus On Green Binary Computer Code Background Canstock
Viruses When Trojan horses can propagate freely and insert a copy of itself into another file, it becomes a computer virus Def A computer virus is a program that inserts itself into one or more files and then performs some action The first phase is called the insertion phase where the virus inserts itself into a file The second phase is called the execution phase where the virus performsOther variants followed The virus originated in the same area of the Philippines as the virus that made the No1 spot on our list 4Oct 28, 02 · Though popularly called viruses, Code Red and many of its notorious predecessors are technically considered worms A virus must incorporate itself into



Code Red Computer Worm Youtube



Computer Invaders 25 Infamous Viruses Over The Last 25 Years Visual Ly
Nimda is a computer worm, and is also a file infector observed in the Internet on September 18, 01 It quickly spread, eclipsing the economic damage caused by past outbreaks such as Code Red Multiple propagation vectors allowed Nimda to become the Internet's most widespread virus/worm within 22 minutes Due to the release date, some media quickly began speculating a link between the virusCode Red is a worm that exploits a security hole in Microsoft Internet Information Server (IIS) to spread When it infects a server it starts to scan for other vulnerable servers and infects them During a certain period of time the worm only spreads, then it initiates a DenialofService (DoS) attack against www1whitehousegov and finallyAug 08, 01 · Computerworld covers a range of technology topics, with a focus on these core areas of IT Windows, Mobile, Apple/enterprise, Office and



Code Red Fixico Blog



Top Most Dangerous Computer Viruses Of All Time
This paper is about fitting a model for the spreading of a computer virus to measured data, contributing not only the fitted model, but equally important, an account of the process of getting there Over the last years, there has been an increased interest in epidemic models to study the speed of virus spreadJul 30, 01 · security specialists said the Code Red computer worm presents a "very real and present threat to the Internet" and warn there were only a few hours left to act before the virusServers Struck by 'Code Red' Virus By David Ruppe July 23 — The US military has blocked public access to nearly all its Web sites after its servers were attacked by a new computer virus



The Most Famous Or Infamous Viruses And Worms Of All Time Eweek


Code Red Computer Virus By Katie Aranda
VIRUS CODE RED Code Red menginfeksi hampir seluruh komputer di dunia pada tahun 01 Code Red berhasil merusak website whitehousegov dan memaksa badanbadan pemerintah lainnya untuk membackup datanya sementaraMar 04, 15 · CODE RED is a worm, so it spreads quickly and sneakily CODE RED can spread on internet connection to any users on an infected site or server CODE RED was launched on July 15, 01 in America http//wwwsymanteccom/security_response/writeupjsp?docid=01Aug 31, 01 · The Code Red worm spread by infecting computers that run Microsoft IIS, a corporate internet software programme that contained a security hole The company released a patch to fix the flaw and



What Is Virus Code Red How To Remove Like



Code Red Archives Foreign Policy
Jul 05, 13 · The Code Red worm, July 01 This devilish little creation infected tens of thousands of systems that ran Microsoft Windows NT and WindowsJul , 01 · WASHINGTON An Internet virus dubbed "Code Red" failed to shut down the White House website, even after marshaling the power of hundreds of thousands of computers in its attack The virus hasAug 28, 01 · The Defense Department continues to monitor its fortified computer systems for the socalled Code Red "worm" virus and its variants, the Pentagon's chief information officer said on



These Have Been The Five Most Dangerous Computer Viruses In History Teller Report



Worm W32 Codered F Description F Secure Labs
Nimda is a malicious fileinfecting computer worm It quickly spread, surpassing the economic damage caused by previous outbreaks such as Code Red The first released advisory about this thread (worm) was released on September 18, 01Aug 29, 01 · The most notable is Code Red, but potentially more damaging are Code Red II and SirCam Together, these attacks have infected millions of computer users, shut down websites, slowed Internet service, and disrupted businesses and government operationsApr 26, 21 · Collection of ancient computer virus source codes virus malware Updated Nov 3, ;


What Is Code Red


Top 10 Worst Viruses Page 2 Of 3 Realitypod
MinhasKamal / StupidKeylogger Star 325 Code Issues Pull requests A Terrific Keystroke Recorder java windows virus trojan spyware keylogger pendrive fud UpdatedJul 05, 06 · Code Red was a computer worm that was unleashed on network servers on July 13, 01 It was a particularly virulent bug because of itsMy problem NOW is twice a RED screen took over my computer It happened today again when I was in Chrome, looking at extensions I couldn't get out of it until I shut down my computer


New Windows Virus Infects Millions Of Computers Technollama



Five Of The Worst Computer Viruses Prior To Heartbleed
This caused each infected computer to infect a different list of randomly generated IP addresses Wh ile thi s change seems m inor, the were vulnerable to Denial of Service due to the Code Red virus These devices were not infected with Code Red, but would crash or reboot when they were sent a copy ofAug 06, 01 · E xperten haben am Wochenende eine neue und möglicherweise gefährlichere Variante des InternetVirus „Code Red" entdeckt Der Virus funktioniere nach dem Prinzip, dass er Computer befalle · The Code Red Virus The Code Red worm was a "file less" worm—it existed only in memory and made no attempt to infect files on the system Taking advantage of a flaw in the Microsoft Internet Information Server, the fastreplicating worm wreaked havoc by manipulating the protocols that allow computers to communicate and spread globally in just



10 Deadliest Computer Viruses Of All Time Hongkiat



Code Red Hd Stock Images Shutterstock



Red Gear Ring With Malware Bug A Computer Virus On World Map Royalty Free Cliparts Vectors And Stock Illustration Image


What Is A Virus Check Point Software



Concept Computer Virus Binary Code Red Stock Photo Edit Now



Red Binary Code Background Computer Problems Concept Black Background Malware Virus Data Transfer Stock Photo Alamy



How To Create A Virus 9 Steps With Pictures Wikihow


Code Red Computer Virus By Vipin Gaji



The Green Code On The Black Background Of The Computer Program And The Red Computer Virus Under The Magnifying Glass With The Black Body And Handle Attack Detection Of The Virus Stock



Worm W32 Codered Description F Secure Labs



9 Most Deadly Computer Viruses Ever Discovered



What Is Code Red Worm How To Remove Codered Worm From Pc



15 Most Dangerous Computer Viruses Boredbug



Top 10 Most Dangerous And Destructive Cyber Viruses Of All Time



Computer Virus Text On Binary Code Stock Illustration



Corrupted Data Red Binary Code With Missing Pieces Computer Stock Photo Picture And Royalty Free Image Image



Computer Virus Pictures Download Free Images On Unsplash



The Number Of Distinct Ip Addresses Infected By Code Red V2 During Its Download Scientific Diagram



Virus Stock Photo Download Image Now Istock



Red Gear Ring With Malware Bug A Computer Virus On World Map On Binary Code Background Vector Illustration Security Technology Concept Canadian Underwriter Canadian Underwriter



Pin On Computer Security



Top 5 Weird Computer Viruses Over The Years Augusta Computer Experts



The Top 10 Worst Computer Viruses In History Hp Tech Takes



Vector Stock Comuter Laptop With Malware Bug A Computer Virus On Red Binary Code Background Vector Illustration Security Technology Concept Clipart Illustration Gg Gograph
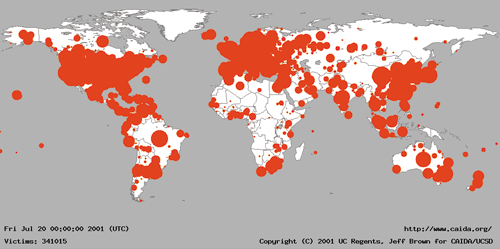


Caida Analysis Of Code Red Caida



Code Red Archives Foreign Policy



Infographic What Is Attacking My Computer Omega Computer Services



Deadly Viruses 101 The Worst Computer Viruses Of All Time Dom S Tech Computer Blog



What Is A Computer Virus And 5 Signs You Re Infected Cso Online



Red Of Ring And Gears With Malware Bug A Computer Virus Inside On Binary Code Background Vector Illustration Security Canstock



Giuliano Liguori Deadliest Computer Viruses Of All Time T Co Y6zrms3bfy Via Ingliguori Cybersecurity Cybercrime Cyberattack Infosecurity Dataprotection Darkweb Devcommunity Linux Ransomware Virus Infosec Antgrasso


How To Make A Code Red Virus Youtube



Code Red Virus Hulyo 12



Cyber Threat List Of Latest Computer Viruses 21



Top 5 Most Dangerous Computer Viruses Ever By



Computer Virus And Binary Code Stock Photo Image By C Vladru



What Is Code Red Worm How To Remove Codered Worm From Pc
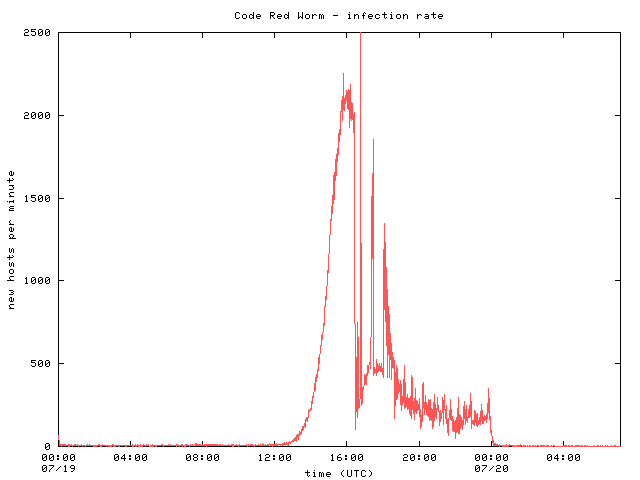


The Spread Of The Code Red Worm Crv2 Caida



The Most Notorious Computer Viruses
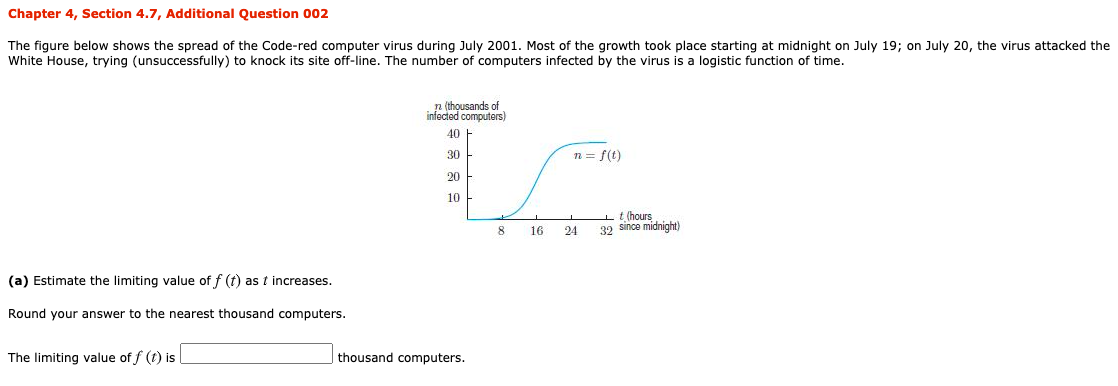


Solved Chapter 4 Section 4 7 Additional Question 002 Th Chegg Com


Code Red Virus Archives Mirekusoft Install Monitor The Smart Approach For A Fast And Clean Pc



Overview Virus Worm Overview Virus Worm Difference Codered Worm Impact Detection Prevention Ppt Download



10 Worst Computer Viruses Of All Time Howstuffworks



Computer Virus Infection Rows Binary Codes Randomly Colored Red Blue Stock Photo Image By C Suebsiri



24 225 Computer Virus Illustrations Clip Art



Computer Virus Infection Rows Of Binary Codes Randomly Colored Red And Blue On Black Screen Monitor Background Corrupted Computer Data Bad Sector Ha Stock Photo Alamy


Computer Virus Catalog


Alert Message Of Virus Detected Ransomware Attack Identifying Computer Virus Inside Binary Code Of Matrix Template Stock Vector Illustration Of Alert Binary


New Scam Microsoft Warning Alert


Top 10 Worst Viruses Page 2 Of 3 Realitypod



Attack Of Code Red Virus Shipou


Code Red Et Al


About The Code Red Worm Chicago Tribune



Red Skull Virus On Binary Computer Code Stock Photo Download Image Now Istock



Computer Virus Binary Code Wire With Red Viruses 3d Illustration Stock Photo Image By C Fredex


Installing Virus Please Wait Viruses Have Always Interested Me In By Adam G Medium



Virus Text On Random Binary Code Red Screen Computer Technology Stock Photo Picture And Royalty Free Image Image


What Is The Most Dangerous Computer Virus Ever Created Quora


Viruses Computer Safety



Pin On Ccc Concepts And Terminologies



14 Infamous Computer Virus Snippets That Trace A History Of Havoc Zoodroid Blogspot Com Technews Spot



Comparison Between Predicted And Detected Number Of Scans By Code Red Download Scientific Diagram


05 Dangerous Computer Viruses Ever Faq For Freshers
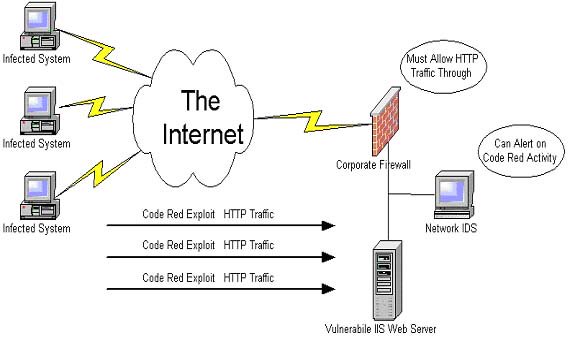


Sans Institute


Computer Virus Red Binary Code Wire With Green Viruses 3d Illustration Stock Images Page Everypixel
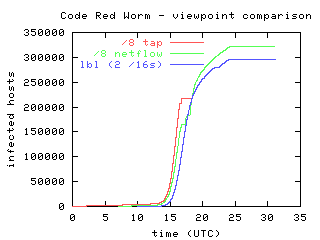


The Spread Of The Code Red Worm Crv2 Caida



Code Red Virus



Wannacry Ransomware Attack Wikipedia



Comtechedu



Red Skull Virus On Binary Computer Code Stock Illustration Illustration Of Media Electronic



Virus Detected Alert Image Photo Free Trial Bigstock



9 Types Of Malware And How To Recognize Them Cso Online


Code Red Worm Not Made In China



Virus Code Stock Illustrations 28 934 Virus Code Stock Illustrations Vectors Clipart Dreamstime



Solved 13 The Figure Below Shows The Spread Of The Code Chegg Com


What Is Virus Code Red How To Remove Like



10 Deadliest Computer Viruses Of All Time Hongkiat



Code Red Virus



Binary Blue The Word Red Virus Computer Virus Concept Binary Code Background Stock Illustration Illustration Of Background Monitor



Code Red Virus



10 Deadliest Computer Viruses Of All Time Hongkiat



Code Red Worm Throwback Tech Thursday Code Institute



The Code Red Code Red Ii Computer Virus 01 Computers Demystified



No comments:
Post a Comment